The RADIUS scheme applies the Remote Authentication Dial-In User Service (RADIUS) protocol in order to manage the exchange of authentication information in the internal network. When using a RADIUS server for authentication in Forefront Unified Access Gateway (UAG), the RADIUS authentication server and Forefront UAG operate in a client-server mode, whereby Forefront UAG is configured as a client of the RADIUS server.
Secret key
The RADIUS protocol utilizes a secret key to encrypt the credentials that the user enters in the login script. The authentication server then decrypts the data and compares it to its database.
Challenge-response modes
The RADIUS authentication scheme supports all the challenge-response authentication modes available on the RADIUS server; for example, allowing the user to create a new personal identification number (PIN), requiring the user to create a new PIN, requiring the user to enter the token that is displayed on the authenticator, and more.
RADIUS groups
You can configure the RADIUS authentication scheme to extract users' group membership from a RADIUS attribute.
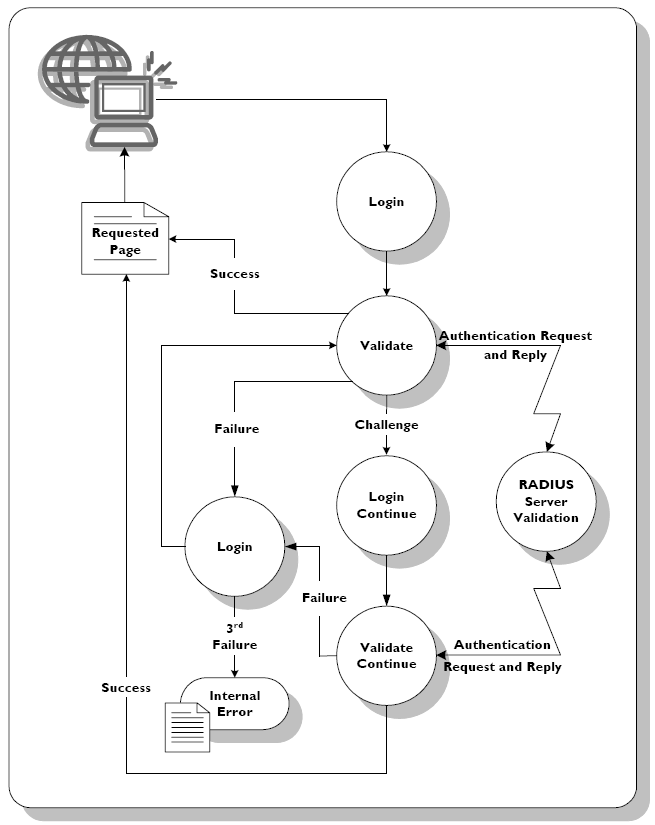
RADIUS authentication flow
The following figure illustrates a sample authentication process through which users pass when the RADIUS authentication scheme is implemented in a challenge-response mode. In this mode, the user can be challenged a number of times before the request is accepted, depending on the configuration of the RADIUS server.
 Note: Note: |
|---|
| The flow allows for three login attempts, after which login failure is final. The actual number of login attempts users are allowed is configurable. |
RADIUS Authentication Scheme--Sample Flow